Disclaimer With constant change being the only consistency in the Cloud engineering space, this tutorial is no longer possible due to the 2 major changes.
- The change in the total space available in a CloudShell session which is now 1gb making it too small to run Prowler as intended in this tutorial.
- With the new Prowler v3 deprecating the HTML output page makes it not possible to quickly have an overview of the output of Prowler.
We still decided to publish this blog because we believe that the reasoning behind why using a tool such as Prowler can have a positive impact on your security posture when it comes to your AWS environment.
With that being said, stay tuned for an updated version where we will review the new Prowler v3 dashboard functionality.
Introduction to Security Scanning
Cloud computing offers numerous benefits, including scalability, flexibility, and cost-efficiency. However, it also introduces unique security challenges, such as the risk of data breaches, misconfigurations, and vulnerabilities. Security scanning plays a critical role in identifying and mitigating these risks, helping companies maintain a secure and resilient cloud environment.
Why Prowler and AWS CloudShell
In this post, we are going to explain how to create a security report of an AWS environment using Prowler and the AWS CloudShell. “AWS CloudShell” is a browser-based shell environment that enables users to manage AWS resources directly from the AWS Management Console, without needing to install or configure any additional software.
Prowler is an open-source security tool to perform AWS, GCP and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. Organizations use Prowler for various purposes:
- Comprehensive Security Assessments: Prowler provides a set of checks covering various aspects of AWS security.
- Customizable checks: There is a variety in built-in checks based on various compliance standards.
- Scalability: Prowler is able to handle small to large AWS environments, with one or multiple AWS accounts and regions.
The combination of Prowler and AWS CloudShell allows you to get an understanding of the current security posture of a workload in a rapid and efficient approach.
Before you start
You will need either an IAM role or IAM user with the following permissions in the account you want to run the scan in:
- Read-Only Access
- CloudShell Access
Prepare CloudShell & Install Prowler
In the search tab in the console, type and select CloudShell or click the CloudShell icon located in the top right of the AWS console.
If you have never used the AWS CloudShell service before you might see the following screen. You can safely close it after reading the welcome message.
Once closed, you will see the CloudShell terminal.
In the CloudShell terminal type pip install prowler.
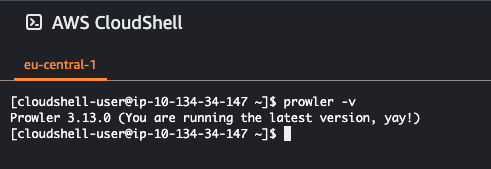
Once the installation is completed run the following command prowler -v to see if the installation is successful.
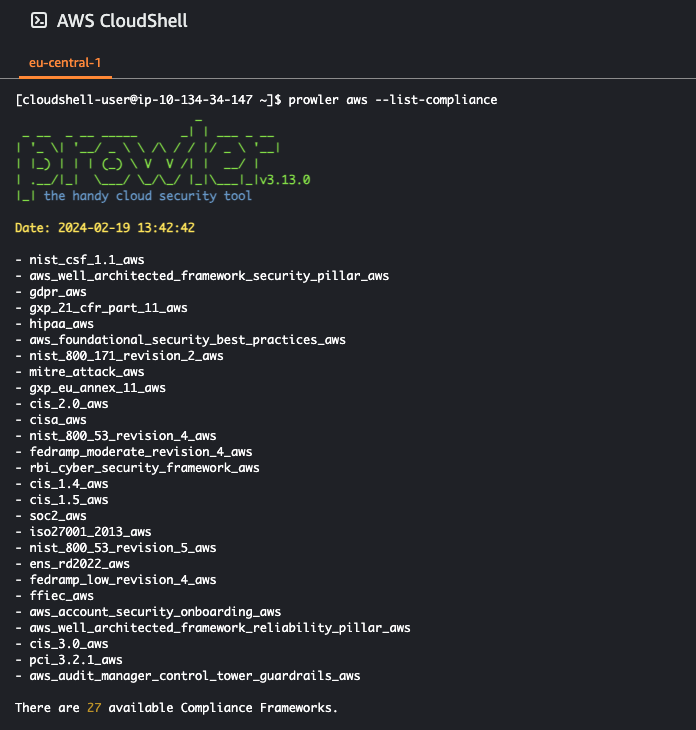
Now that Prowler is installed, we can perform a scan of the account. Prowler offers over 20 Compliance frameworks in which you can use to execute your scan. You can view the entire list by running prowler aws --list-compliance.
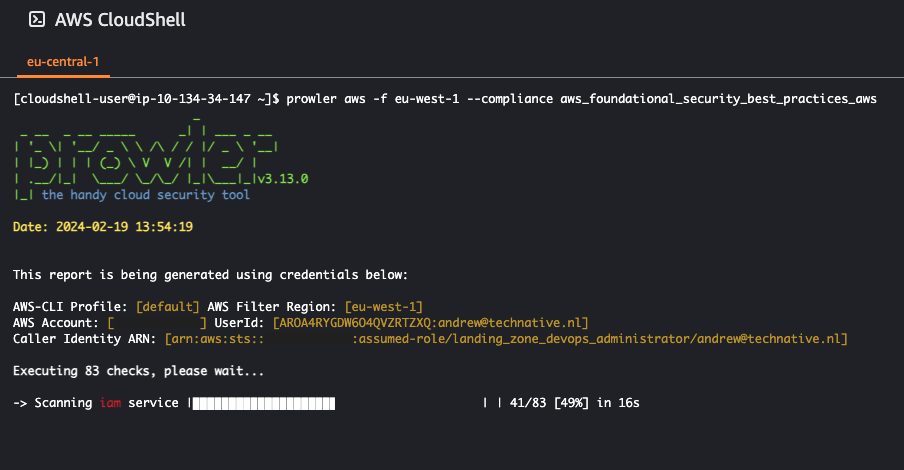
For our Well Architected reviews we tend to use a combination of the NIST, Well Architected Security pillar and AWS foundational security best practices frameworks. Feel free to try any framework you prefer, however for this example we will use the ‘aws_foundational_security_best_practices_aws’ framework. you can read more about FSBP framework here.
Run prowler aws -f eu-west-1 --compliance aws_foundational_security_best_practices_aws to start the scan.
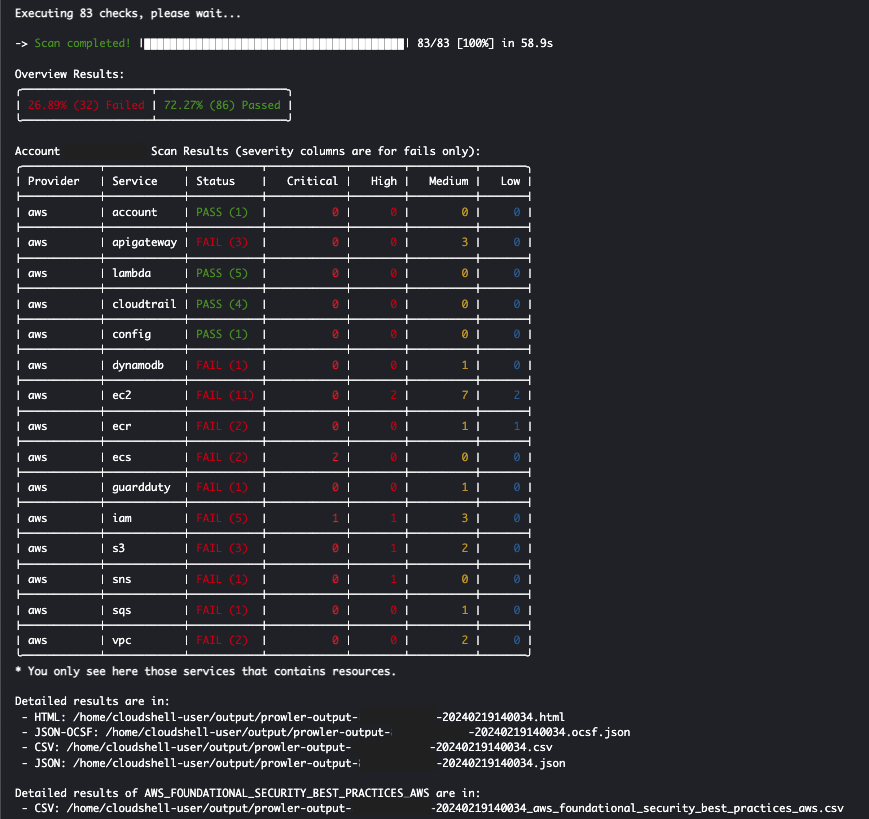
Once completed you will see an overview of the scan and the location where the detailed results are stored in various file types.
Now that our scan is complete and we know the location of our files it’s time to zip them and download them locally to our machine.
- Run
cd outputto change directory to the directory where all the Prowler files are stored. - You can confirm this by running
lsand you should see various files with the name starting with prowler-output. - Run the command
zip prowler-output.zip *to zip all the files in the output directory.
Now that we have zipped the directory, let’s export it to our local machine.
- First get the full path of the zip file by running
readlink -f prowler-output.zip. - Note down the location somewhere as we will be needing it in the next step.
- On the top right of the AWS CloudShell console click on the Actions button.
- In the actions tab click on Download File and paste the path received from the readlink command.
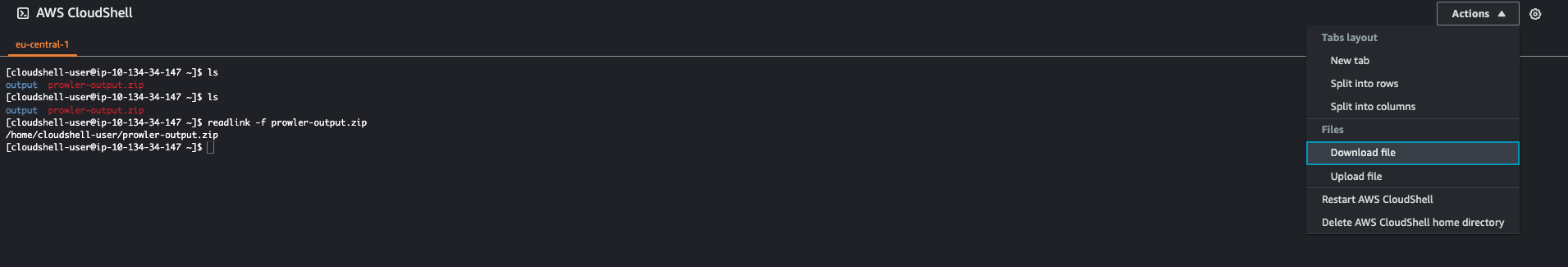
Now that you have downloaded the zip file, proceed to unzip the file and view the detailed outcome of your scan. I like to open the prowler-output file ending with html using a web browser to view the report.
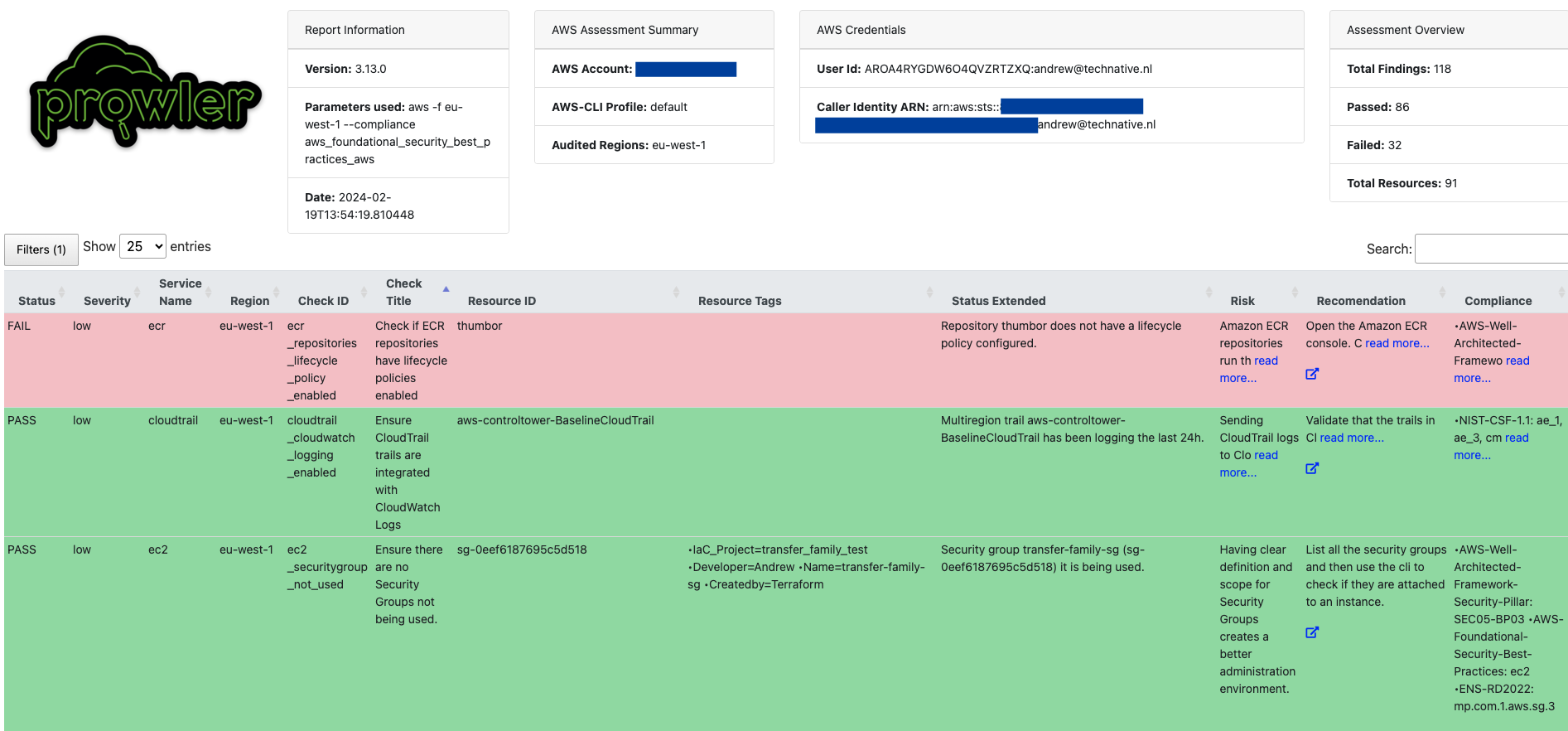
The report shows us various details on the findings. One nice feature is that you can use the filter button to filter the findings based on various points such as Severity status, Compliance or ID. Key details we find important in reviewing such a report are:
- Whether a compliance rule is a pass or fail.
- The severity in failing or passing a rule.
- The risk of the rule.
If you want to continue using Prowler further in your AWS environment consider adding the “Prowler Integration” to import findings to your “AWS Security Hub”.
A must tool for us at TechNative when getting introduced to a new environment and need to get up to speed quickly in terms of the security posture of the AWS environment. By leveraging the capabilities of Prowler, teams can perform comprehensive scans covering various aspects of AWS security and different compliance standards. The scalability of Prowler allows it to accommodate small to large AWS environments across multiple accounts and regions.
In conclusion, the utilization of Prowler in conjunction with AWS CloudShell offers a streamlined and effective method for conducting security assessments within AWS environments. I hope this tutorial will help organizations continue to prioritize cloud security, incorporating tools like Prowler into their workflows to contribute in maintaining a robust and resilient AWS environment.
References:


